Principles of Network Applications
1. Network Application Architectures
An application architecture is designed by application developer and dictates how the application is structured over the various end system. There are two predominant architectural paradigms used in modern network applications: the client-server architecture or the peer-to-peer (P2P) architecture.
- Client-server architecture (Web, FTP, e-mail)
- Server has a permanent IP address.
- clients do not directly communicate with each other, but with server.
- P2P architecture: application exploits direct communication between pairs of intermittently connected hosts.
- Self-scalability: new peers bring new service capacity by distributing files to other peers.
- Challenges
- ISP Friendly: P2P applications such as video streaming and file distribution sometimes put significant stress on the ISPs.
- Security: P2P applications can be challenge to secure due to the highly distributed nature.
- Incentives: The success of future P2P applications also depends on convincing users to volunteer bandwidth, storage and computation resources, which is the challenge of incentive design.
2. Process Communication
- Process: processes in different hosts communicate by exchanging messages.
- client process: process that initiates communication
- server process: process that waits to be contacted
- Socket: process sends/receives messages to/from its socket.
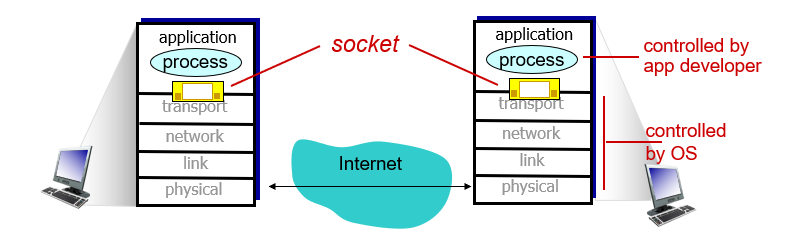
- Addressing process: To identify the receiving process, two pieces of information need to be specified - (1) the address of the host and (2) an identifier that specifies the receiving process in the destination host.
- IP address: a 32-bit quantity that uniquely identifying the host.
- Port number: used to identify the receiving process.
3. Transport Services Available to Applications
Developers need to pick the protocol with the services that best match your application's needs.
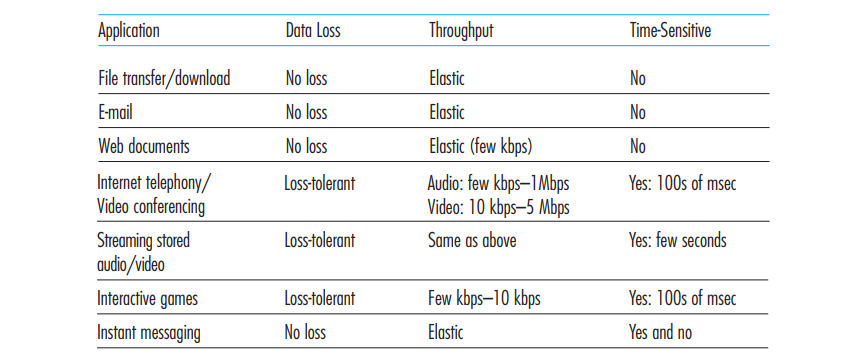
- Reliable data transfer: some apps (e.g. file transfer, web transactions) require 100% reliable data transfer, while other apps (rea-time audio/video) can tolerate some loss.
- Throughput: some apps (e.g., multimedia) require minimum amount of throughput to be “effective”, while other apps (“elastic apps”) make use of whatever throughput they get.
- Timing: some apps require low delay to be "effective"
- Security: a transport protocol provide an application with one or more security services.
4. Transport Services Provided by the Internet
Two transport protocols, UDP and TCP, will be available to applications.
- TCP: TCP has the client and server exchange transport-layer control information with each other before the application-level messages begin to flow.
- A TCP connection is said to exist between the sockets of the two processes.
- Reliable data transfer service: TCP deliver all data sent without error and in the proper order.
- UDP: UDP is a connectionless (no handshaking), lightweight transport protocol providing minimal services.
- Unreliable data transfer: no guarantee that the message will reach the receiving process, and the receiving process may arrive out of order.
5. Application-Layer Protocols
An application-layer protocols defines - the types of messages exchanged - the syntax of the various message types - the semantics of the fields (the meaning of the information in the fields) - rules for determining the sending messages processes
Web and HTTP
1. Overview
- Web page consists of basic HTML-file which includes several referenced objects.
- HTTP (Hypertext Transfer Protocol) is a web's application layer protocol using client/server model
- client: browser that requests, receives, and displays web objects
- server: web server sends objects in response to requests
- HTTP uses TCP as its underlying transport protocol.
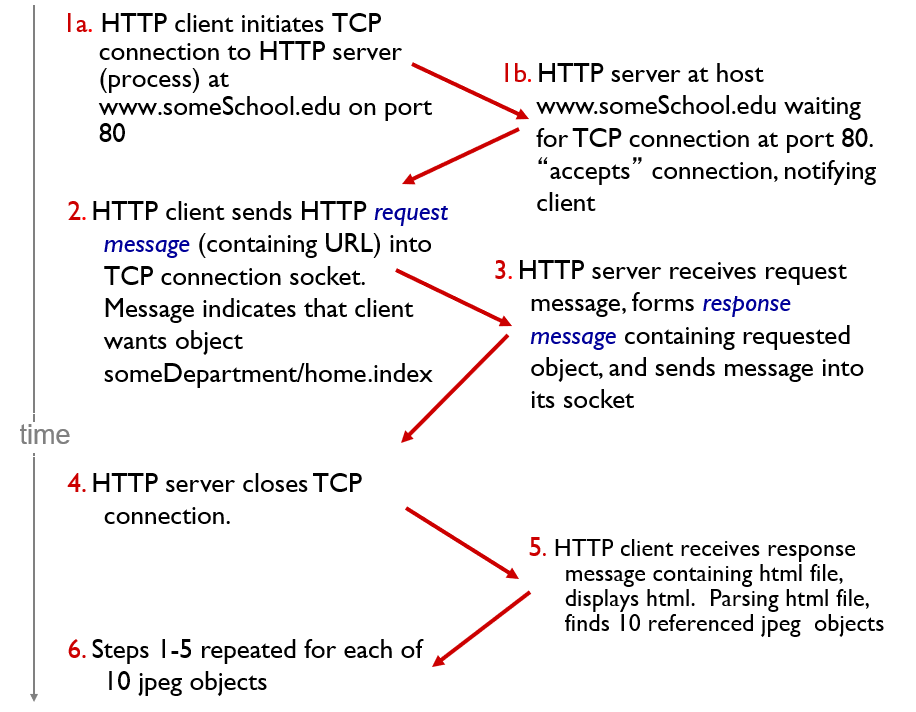
- client initiates TCP connection (creates socket) to server, port 80
- server accepts TCP connection from client
- HTTP messages (application-layer protocol messages) exchanged between browser (HTTP client) and Web server (HTTP server)
- HTTP is a stateless protocol
- An HTTP server maintains no information about the clients.
2. HTTP Connections
Non-Persistent Connections
Each TCP connection is closed after the server sends the object (the connection does not persist for all objects).
Downloading multiple objects required multiple connections.
- Each TCP connection transports exactly one request message and one response message.
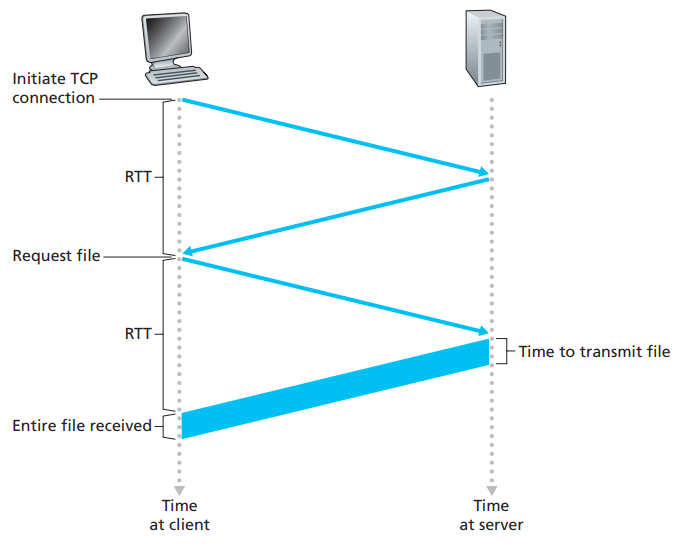
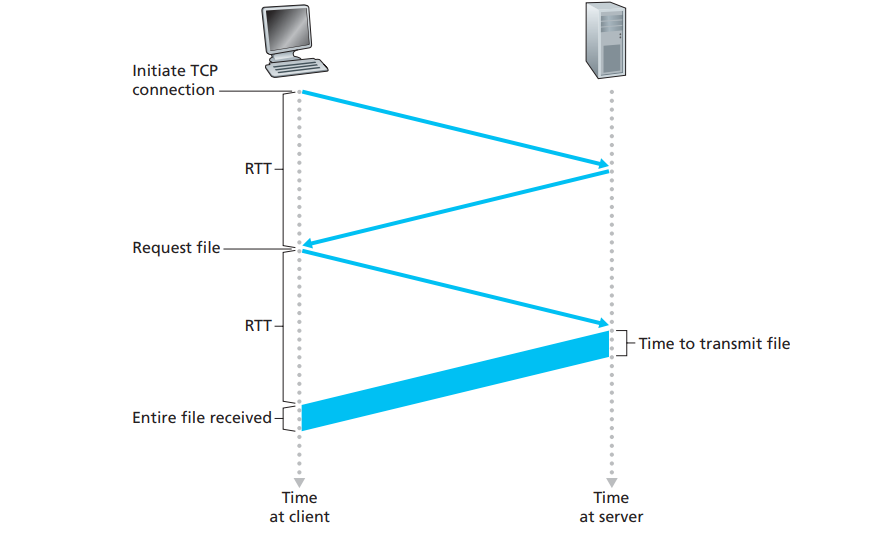
- Round-trip time (RTT): the time it takes for a small packet to travel from client to server and then back to the client.
- Non-persistent HTTP response time = 2 RTT + file transmission time
Persistent HTTP
- Issues of non-persistent HTTP
- a brand-new connection must be established and maintained for each requested object.
- each object suffers a delivery delay of two RTTs
- Persistent HTTP server leaves the TCP connection open after sending a response.
- Subsequent requests and responses between the same client and server can be sent over the same connection.
- Client sends requests as soon as it encounters a referenced object.
- Only one RTT for all the referenced objects.
3. HTTP Message Format
There are two types of HTTP messages: request and response.
Request Message
- HTTP request message generally contains request line, header lines, body.
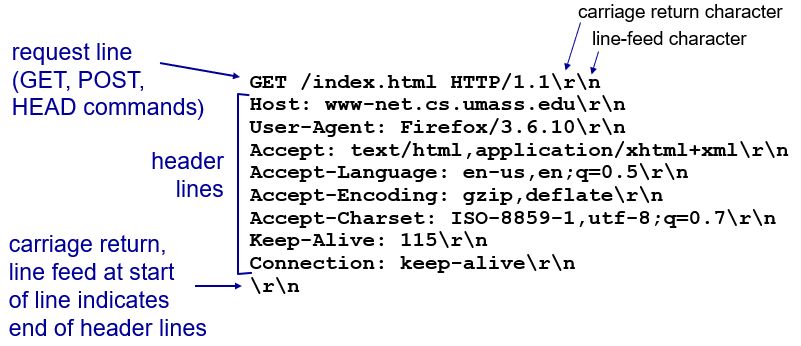
- POST method
- web page often includes form input
- input is uploaded to server in entity body
- GET method
- input is uploaded in URL field of request line www.somesite.com/q=monkeys&banana
Response Message
- HTTP response message format contains status line, six header lines, and then the entity body.
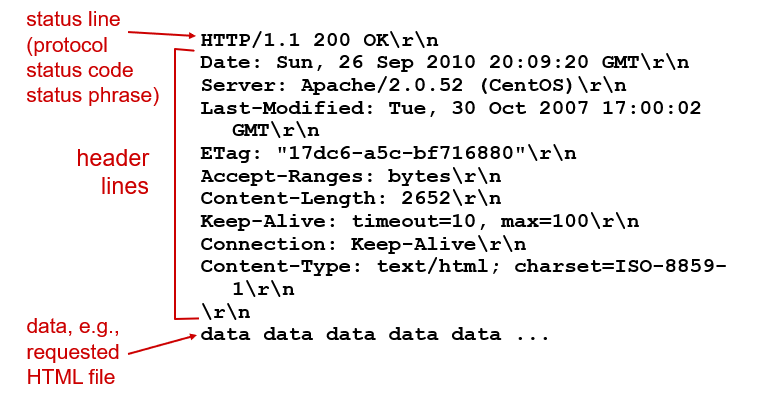
- HTTP response status codes: status code appears in the first line in the response message.
- Some common status codes: 200 --> OK; 404 --> Not Found; 502 --> Bad Gateway.
4. Cookies
An HTTP server is stateless, so that engineers can develop high-performance web servers. However, it is desirable for a Web site to identify users. For these purposes, HTTP uses cookies.
- Cookies are designed to be a reliable mechanism for websites to remember state information.
Cookie technology has four components: 1. cookie header line of HTTP response message 2. cookie header line in next HTTP request message 3. cookie file kept on user's host, managed by user's browser 4. back-end database at web site
Coolie can be used for - authorization - shopping carts - user session state
5. Web Caching (Proxy Server)
A web cache (proxy server) is a network entity that satisfies HTTP requests on the behalf of an origin Web server.
- Cache acts as both a client and a server.
- When it receives requests from and sends responses to a browser, it is a server.
- When it sends requests to and receives responses from an origin server, it is a client.
- Typically cache is installed by ISP (Internet service provider).
- Two reasons for deploying the web caching.
- A web caching can substantially reduce the response time for a client request.
- Web caches can substantially reduce traffic on an institution's access link to the Internet.
6. The Conditional GET
Although caching can reduce user-perceived response times, the object housed in the Web server may have been modified since the copy was cached at the client.
- Cache: specify date of cached copy in HTTP request
- Server: response contains no object if cached copy is up-to-date
FTP
- FTP is a protocol to transfer file to/from remote host.
- client-server model:
- client: side that initiates transfer.
- server: remote host.
- Two parallel TCP connections to transfer a file
- Control connection: sending control information between the two hosts (user identification, password, etc.)
- "out of band": out-of-band data is the data transferred through a stream that is independent from the main in-band data stream.
- Data connection: send files.
- Connection steps:
- FTP client contacts FTP server at port 21;
- Client authorized over control connection;
- Client browses remote directory, sends commands over control connection
- Server opens 2nd TCP data connection to client when server receives file transfer command.
- After transferring one file, server closes data connection.
- Server opens another TCP data connection to transfer another file.
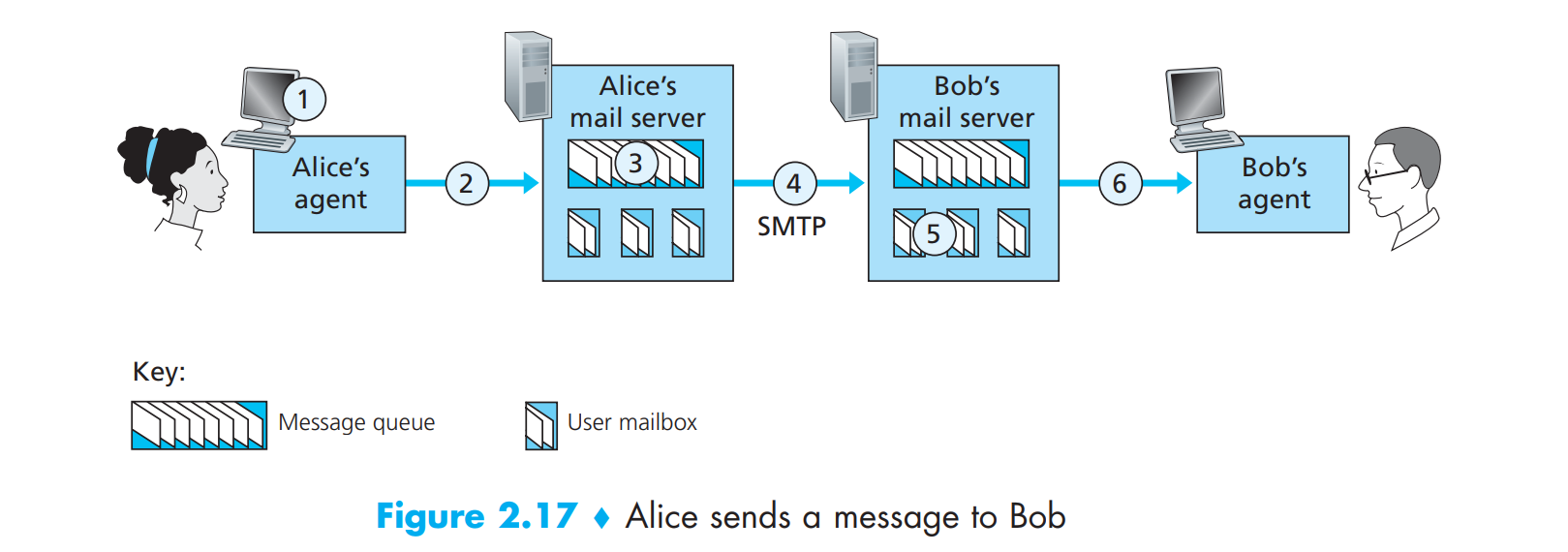
Electronic Mail
There are three major components in the electornic mails: user agents, mail servers, simple mail transfer protocol (SMTP)
User agent (mail reader): composing, reading, mail messages
- Mail server
- Mail server has many mailboxes containing incoming messages for users.
Mail server contains message queue of outgoing mail messages.
1. SMTP
DNS
Domain Name System (DNS): translate hostname to IP address - a distributed database implemented in hierarchy of many name servers - an application-layer protocol that allows hosts to query the distributed database
DNS services: hostname to IP address translation
How DNS Resolve Name?
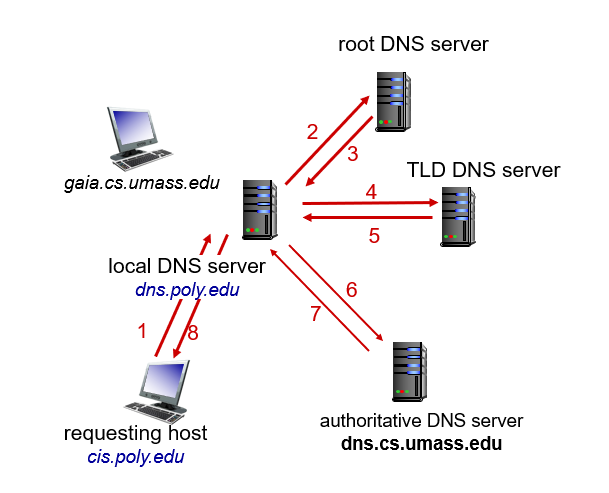
- Local DNS name server: when host makes DNS query, query is sent to its local DNS server.
- each ISP has one (default name server)
- has local cache of recent name-to-address translation pairs
- acts as proxy, forwards query into hierarchy
- Root name server: contacted by local name server that cannot resolve name
- there are 13 root name server strategically deployed around the world
- contacts authoritative name server if name mapping not known
- Top-level domain (TLD) server: responsible for responsible for top-level domains such as .com, .org, .net, .edu, .gov, .top
- Authoritative DNS server: organization's own DNS servers, providing authoritative hostname to IP mapping for organization's named hosts
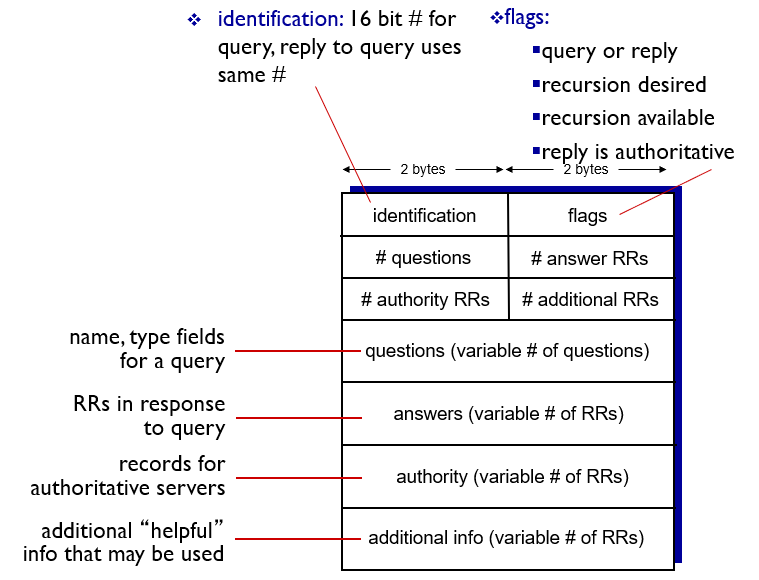
DNS Records and Messages
- Resource records (RR)
RR format: (name, value, type, ttl)
- DNS Messages
P2P Application
P2P architecture allows arbitrary end systems directly communicate with each other.
File Distribution
- In the server-client architecture, peer upload/download capacity is limited due to the constrained bandwidth.
- Server transmission: must sequentially send (upload) N file copies
- time to send one copy: \(F/u_s\)
- time to send \(N\) copies: \(NF/u_s\)
- Client: each client must download file copy
- \(d_{min}=\) minimum client download rate
- minimum client download time: \(F/d_{min}\)
\[ D_{c-s}\geq \max\{NF/u_s,F/d_{min}\} \]
- However, in the P2P architecture, the file distribution time is much less.
- server transmission: must upload at least one copy
- time to send one copy: \(F/u_s\)
- client: each client must download file copy
- min client download time: $F/d_{min} $
- clients: as aggregate must download \(NF\) bits
- max upload rate (limiting max download rate) is \(u_s+\sum u_i\)
\[ D_{P2P}\geq \max\{NF/u_s,F/d_{min}, NF/(u_s+\sum u_i)\} \]
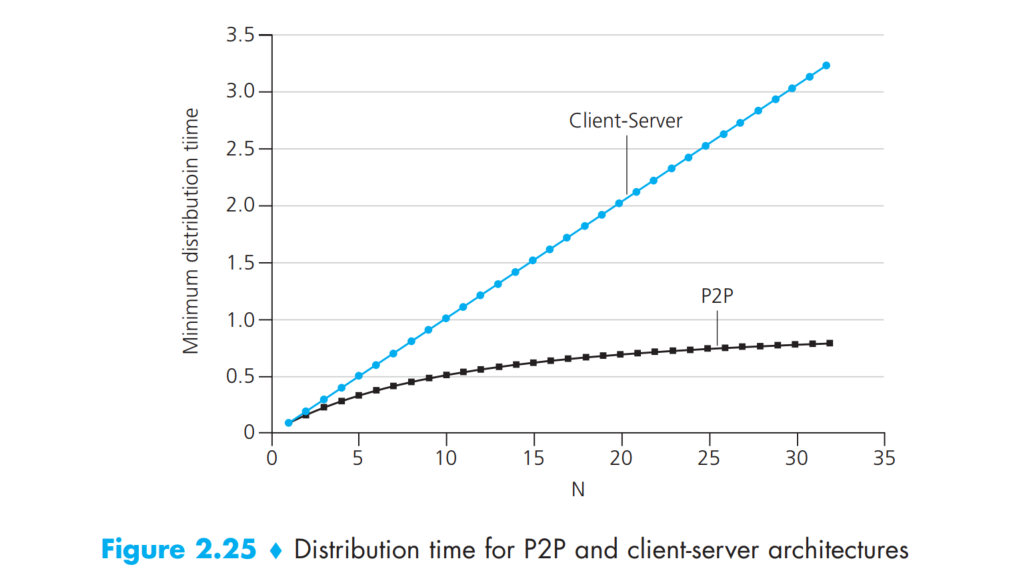
Distribution time for P-2-P and C-S
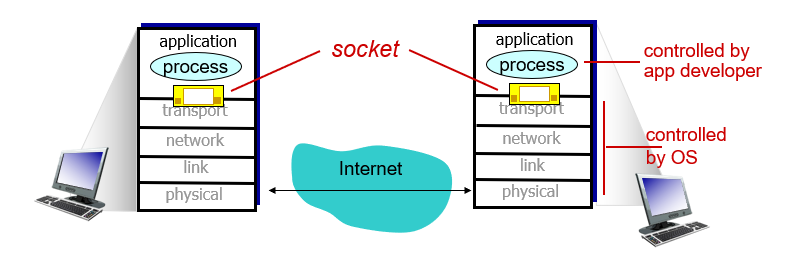
Socket Programming
Socket is a door between application process and end-end transport protocol.
UDP
- UDP does not handshake before sending data.
- sender explicitly attaches IP destination address and port number to each packet.
- UDP transmitted data may be lost or received out-of-order.
- UDP provides unreliable transfer of groups of bytes between client and server.
TCP
- Client must contact server.
- server process must first be running
- TCP provides reliable, in-order byte-stream transfer between client and server.